Modlishka is a flexible and powerful reverse proxy, that will take your ethical phishing campaigns to the next level.
It was realeased with an aim to:
- help penetration testers to carry out an effective phishing campaign and reinforce the fact that serious threat can arise from phishing.
- show current 2FA weaknesses, so adequate security solutions can be created and implemented soon.
- raise community awareness about modern phishing techniques and strategies.
- support other open source projects that require a universal reverse proxy.
Enjoy :-)
Features
Some of the most important 'Modlishka' features :
- Support for majority of 2FA authentication schemes (by design).
- No website templates (just point Modlishka to the target domain - in most cases, it will be handled automatically).
- Full control of "cross" origin TLS traffic flow from your victims browsers (through custom new techniques).
- Flexible and easily configurable phishing scenarios through configuration options.
- Pattern based JavaScript payload injection.
- Striping website from all encryption and security headers (back to 90's MITM style).
- User credential harvesting (with context based on URL parameter passed identifiers).
- Can be extended with your ideas through plugins.
- Stateless design. Can be scaled up easily for an arbitrary number of users - ex. through a DNS load balancer.
- Web panel with a summary of collected credentials and user session impersonation (beta).
- Backdoor free ;-).
- Written in Go.
Action
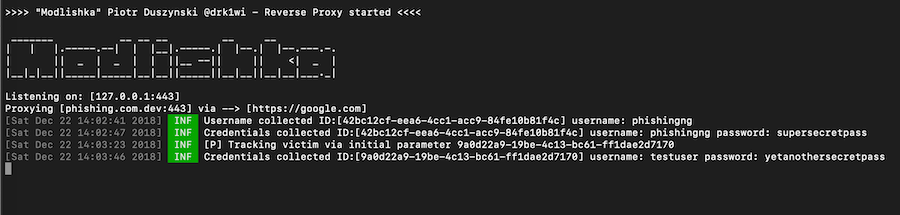
"A picture is worth a thousand words":
Modlishka in action against an example 2FA (SMS) enabled authentication scheme:
Note: google.com was chosen here just as a POC.
Installation
Fetch the code with 'go get' :
$ go get -u github.com/drk1wi/Modlishka
Compile the binary and you are ready to go:
$ cd $GOPATH/src/github.com/drk1wi/Modlishka/
$ make
# ./dist/proxy -h
Usage of ./dist/proxy:
-cert string
base64 encoded TLS certificate
-certKey string
base64 encoded TLS certificate key
-certPool string
base64 encoded Certification Authority certificate
-config string
JSON configuration file. Convenient instead of using command line switches.
-credParams string
Credential regexp collector with matching groups. Example: base64(username_regex),base64(password_regex)
-debug
Print debug information
-disableSecurity
Disable security features like anti-SSRF. Disable at your own risk.
-jsRules string
Comma separated list of URL patterns and JS base64 encoded payloads that will be injected.
-listeningAddress string
Listening address (default "127.0.0.1")
-listeningPort string
Listening port (default "443")
-log string
Local file to which fetched requests will be written (appended)
-phishing string
Phishing domain to create - Ex.: target.co
-plugins string
Comma seperated list of enabled plugin names (default "all")
-postOnly
Log only HTTP POST requests
-target string
Main target to proxy - Ex.: https://target.com
-targetRules string
Comma separated list of 'string' patterns and their replacements.
-targetRes string
Comma separated list of target subdomains that need to pass through the proxy
-terminateTriggers string
Comma separated list of URLs from target's origin which will trigger session termination
-terminateUrl string
URL to redirect the client after session termination triggers
-tls
Enable TLS (default false)
-trackingCookie string
Name of the HTTP cookie used to track the victim (default "id")
-trackingParam string
Name of the HTTP parameter used to track the victim (default "id")


0 Comments