pwndb.py is a python command-line tool for searching leaked credentials using the Onion service with the same name. In this post I’ll describe all the possible options.
Disclaimer
[!] Legal disclaimer: Usage of pwndb.py for attacking targets without
prior mutual consent is illegal. It is the end user's responsibility
to obey all applicable local, state and federal laws. Developers assume
no liability and are not responsible for any misuse or damage caused.
Using a single email:
$ python pwndb.py --target testing@email.com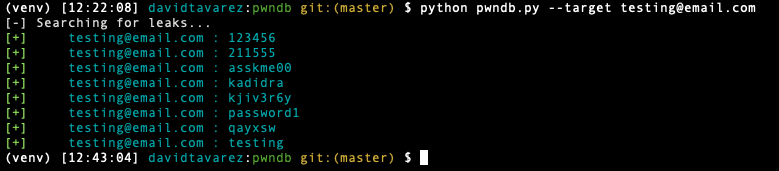
Using a domain name:
$ python pwndb.py --target @testing.com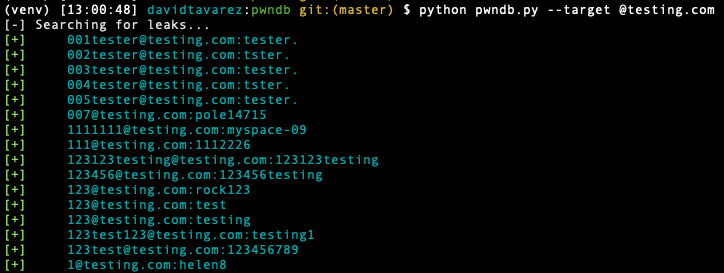
Using a file:
Example file:
juanpapafrancisco@gmail.com, romeoyjulietasantos@hotmail.com, dddd@email.com.do
jhonpope@vatican.com
friend@email.com, John Smith <john.smith@email.com>, Jane Smith <jane.smith@uconn.edu>
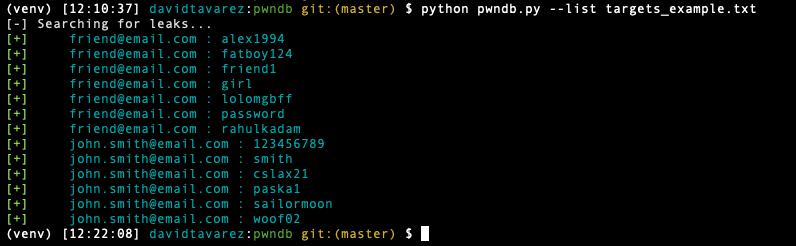
$ python pwndb.py --list targets_example.txt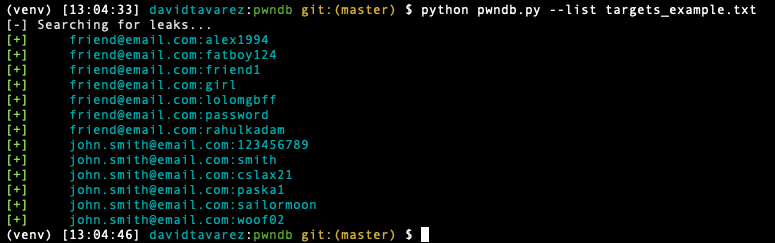
Using %:
$ python pwndb.py --target testing.%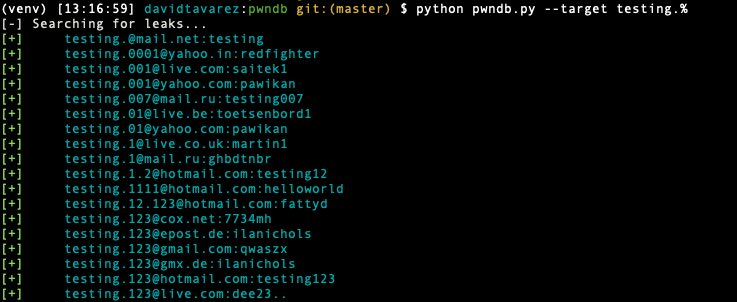



0 Comments